Performing banner grabbing
Exercise 1 - Performing Banner Grabbing
Banners are text-based welcome screens from remote hosts that display system information. Banner grabbing enables you to retrieve information about a computer system on a network and capture banners of open ports. You can perform banner grabbing using tools such as telnet, Netcat, and Nmap.
In this exercise, you will grab banners served by the DVWA application running on port 80 on PLABSA01device. You will use telnet, Netcat and Nmap to perform this technique.
Please refer to your course material or use your preferred search engine to research this topic in more detail.
Task 1 - Enable HTTP Web Service on PLABSA01
In this task, you will enable the HTTP web service on port 80 on the PLABSA01 device. To do this, perform the following steps:
Step 1
Ensure you have powered on the required devices and connect to PLABSA01.
Close the Server Manager window.
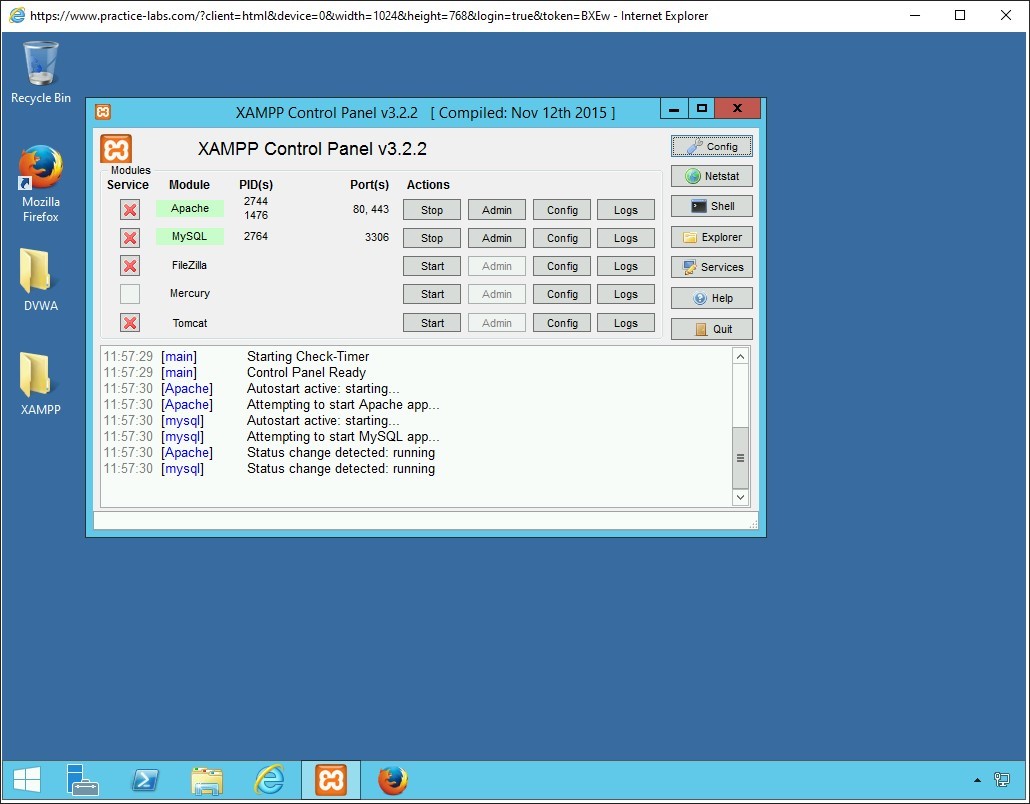
Click the XAMPP application icon from the taskbar.
The XAMP Control Panel v3.2.2 opens.
The Apache web service with Damn Vulnerable Web Application (DVWA) running on port 80 is enabled.
Step 2
Connect to PLABWIN10.
Open Internet Explorer from the taskbar.
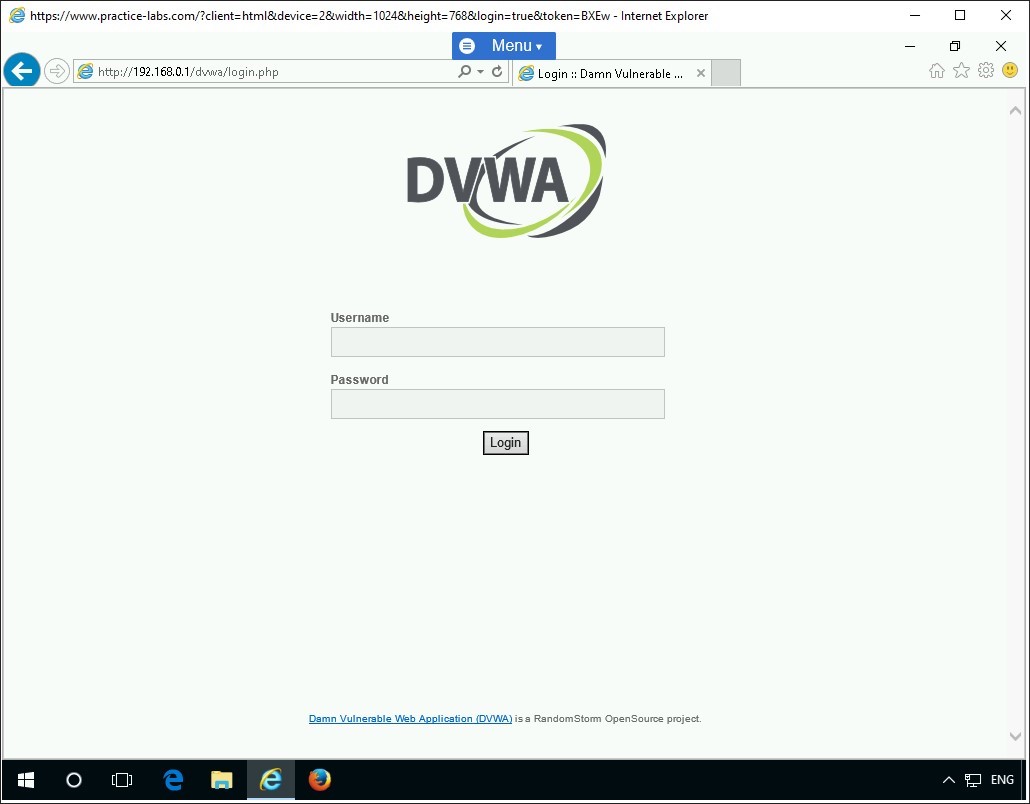
To access the DVWA application on PLABSA01, type the following URL in the address bar and press Enter:
http://192.168.0.1/dvwa/login.php
DVWA login page opens.
Minimize Internet Explorer.
Task 2 - Perform Banner Grabbing using Telnet
In this task, you will use telnet to grab banners served by the DVWA application. Before performing this task, connect to PLABKALI01.
Step 1
Ensure you have powered on the required devices and connect to PLABKALI01.
Type Root in the Username field.
When prompted, type the following password in the Password field:
Passw0rdClick Sign In.
Step 4
From the PLABKALI01 device, double-click the Root Terminal icon on the left taskbar to open a root terminal window.
The root terminal window opens.
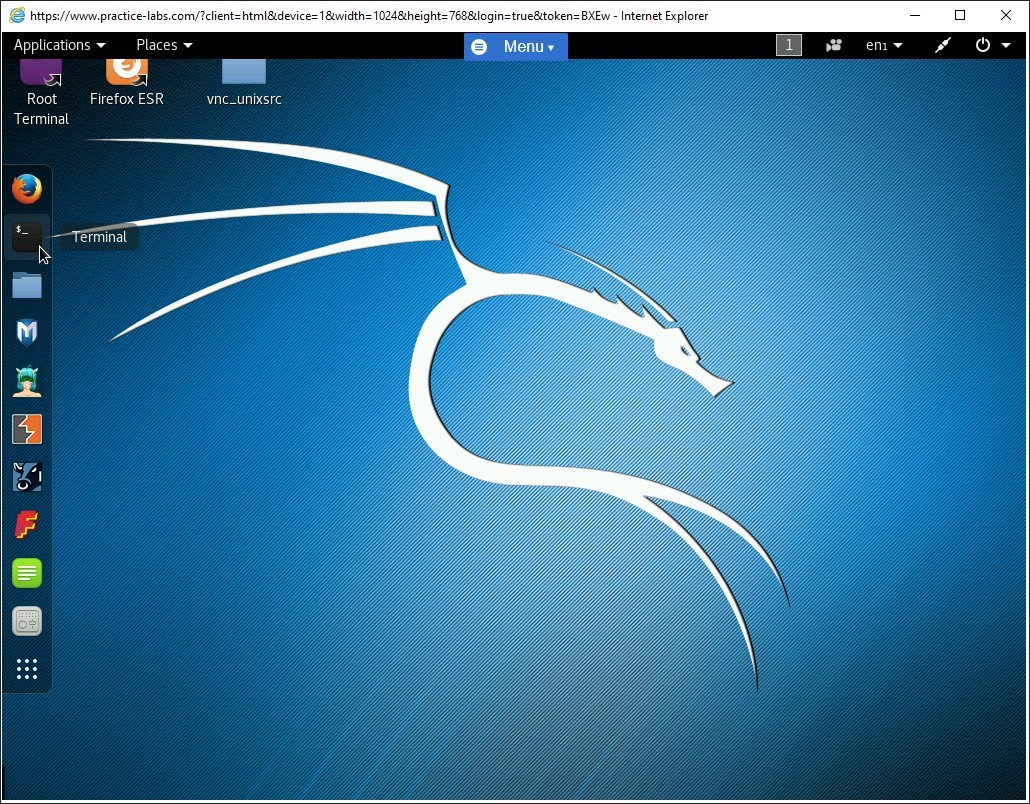
Step 5
Establish a remote connection with port 80 on 192.168.0.1 using Telnet.
Type the following command at the root terminal:
telnet 192.168.0.1 80
Press Enter.
Connection to 192.168.0.1 is established.
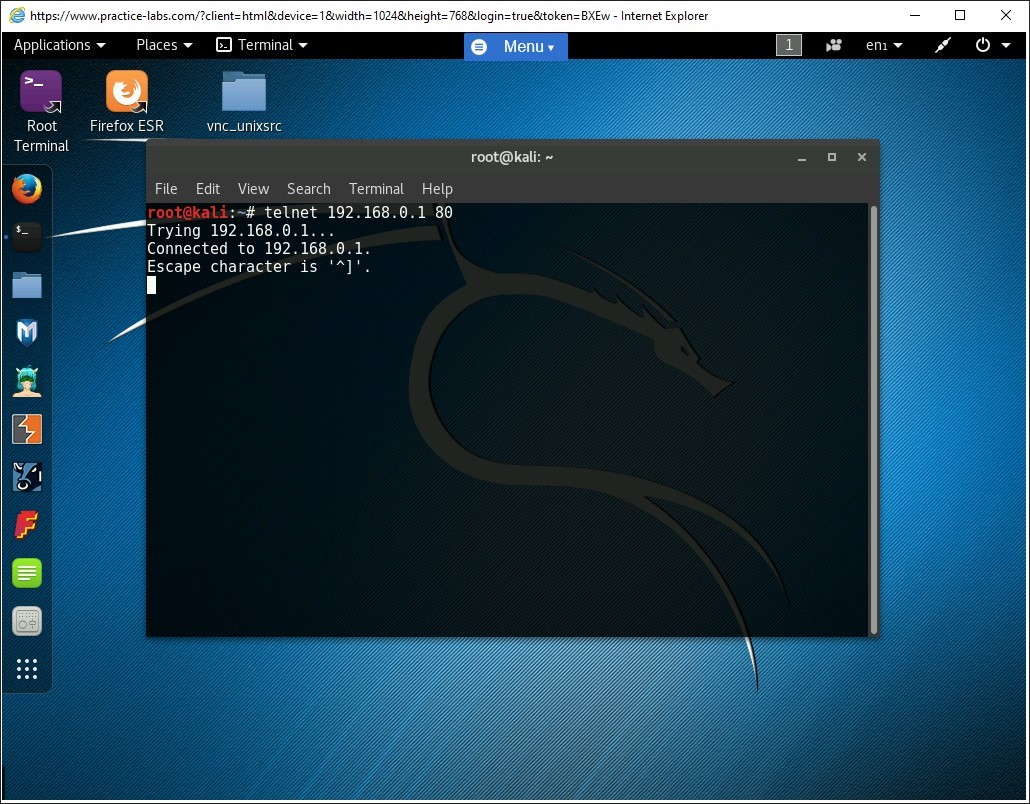
Step 6
To grab the banners served by the DVWA application, type the following command at the root terminal and press Enter:
GET /dvwa/ HTTP/1.1
Then, type the following switch:
Host: 192.168.0.1
Press Enter.
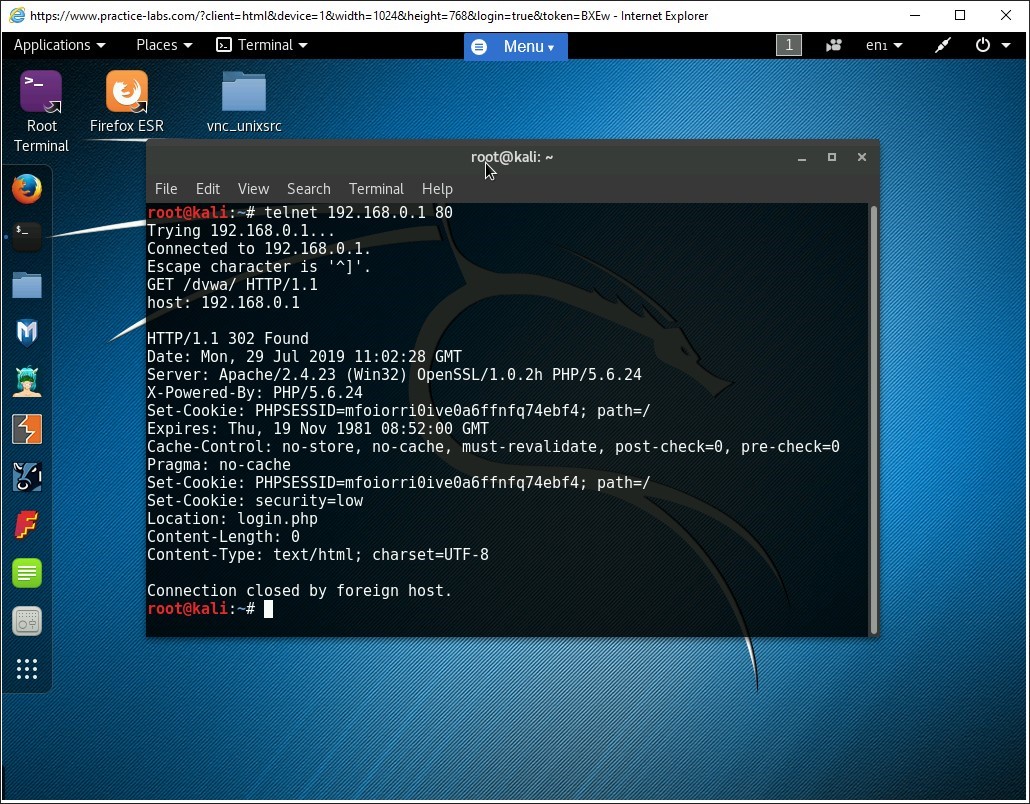
The given command specifies the following switches:
- GET = To obtain data from the web server
- HTTP = Protocol to connect with
- Host = IP address/domain name of the remote host
The command has successfully grabbed the banners served by the web server. Notice the server field in the output specifies the name of the web server, which is in this case, Apache.
Task 3 - Perform Banner Grabbing using Netcat
Netcat (often abbreviated to nc) is a computer networking utility for reading and writing from and to network connections using Transmission Control Protocol (TCP) or User Datagram Protocol (UDP). Netcat can be used for port scanning, transferring files and port listening.
In this task, you will perform banner grabbing using Netcat. To do this, perform the following steps:
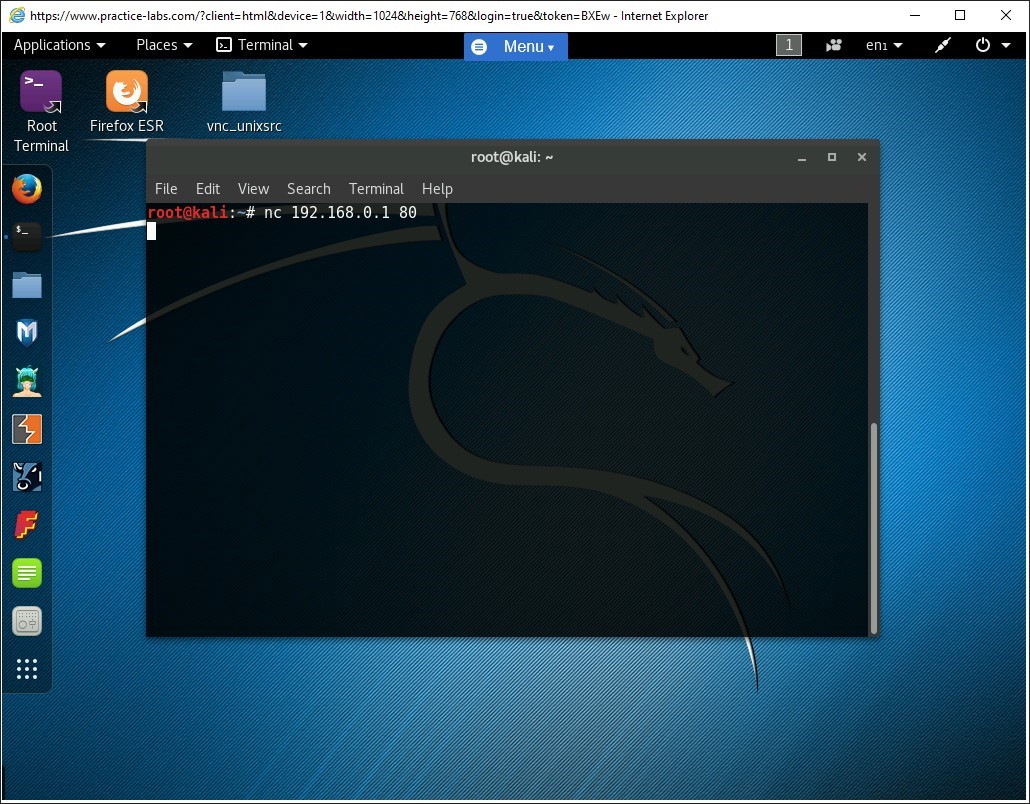
Step 1
Type the following command at the root terminal of Kali Linux and press Enter:
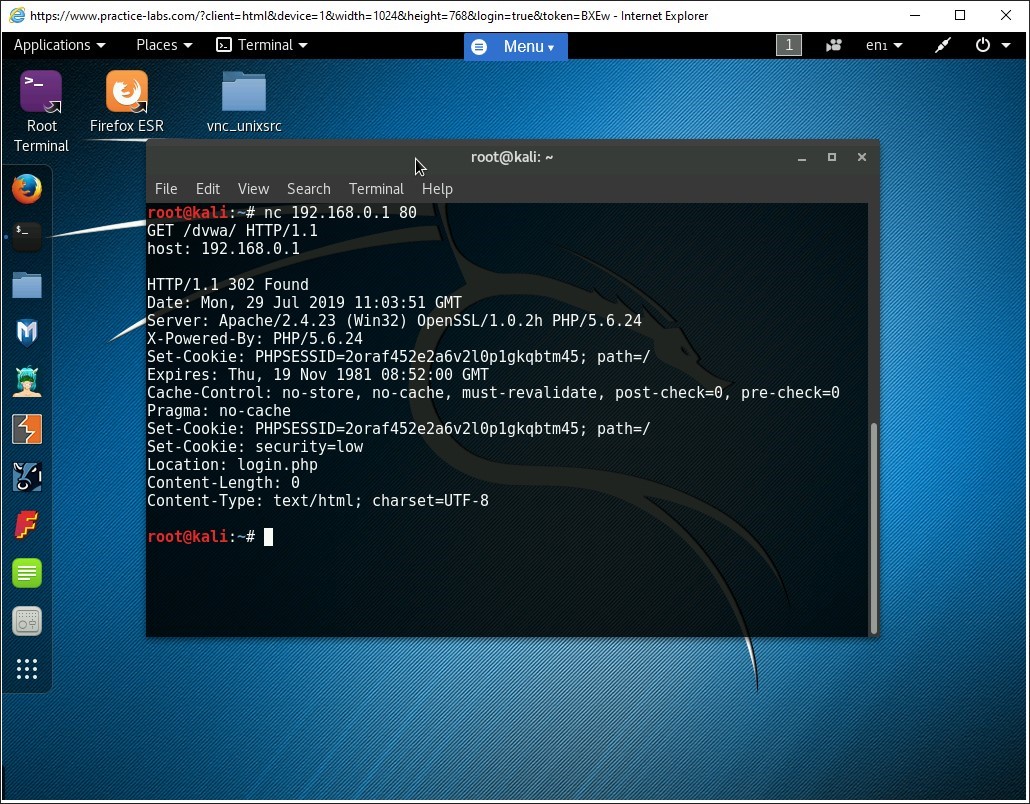
nc 192.168.0.1 80
Step 2
To grab the banner served by the DVWA application, type the following command and press Enter:
GET /dvwa/ HTTP/1.1
Then, type the following switch:
Host: 192.168.0.1
Press Enter.
Alert: Please be aware you may have to type this command in twice for the command to display the results.The command has successfully grabbed the banners served by the web server. Notice the server field in the output that specifies the name of the web server, which is in this case, Apache.
Task 4 - Perform Banner Grabbing using Nmap
In this task, you will grab the banner served by the DVWA application using Nmap. To do this, perform the following steps:
Step 1
Type the following command at the root terminal and press Enter:
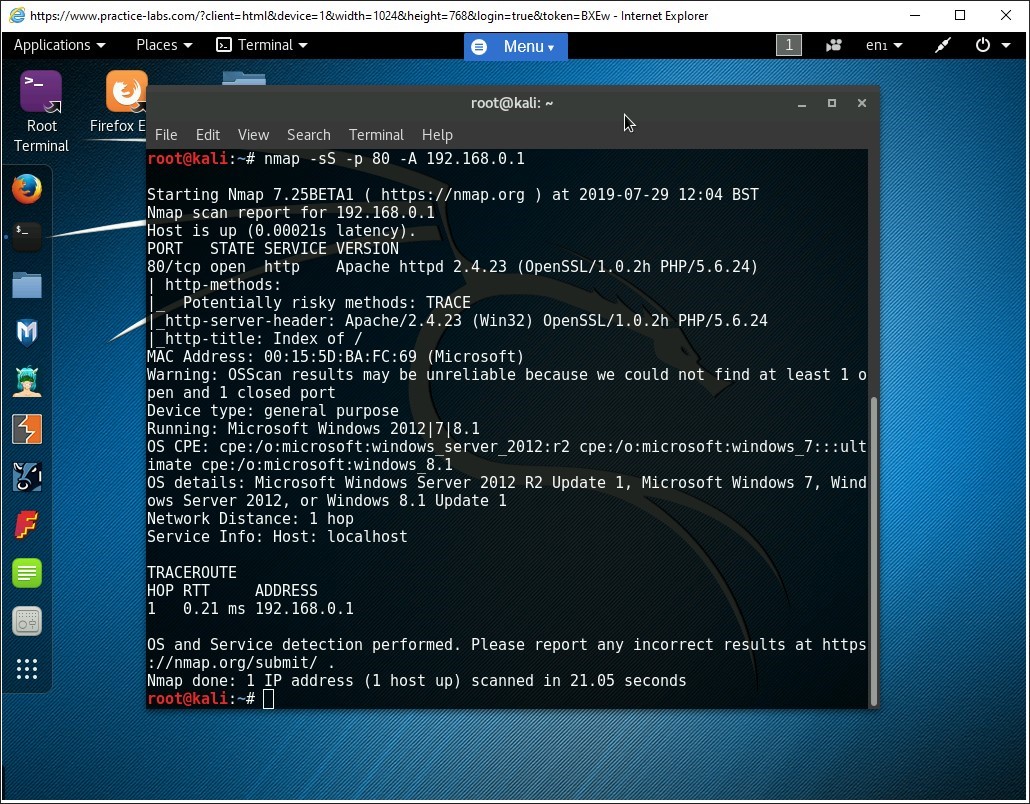
nmap -sS -p 80 -A 192.168.0.1
The given command uses the following switches:
- -sS = SYN Scan
- -p = Port Number
- -A = Aggressive mode
Notice the output displays information about the operating system of the target system and the services running on open ports.
Comments
Post a Comment